Review Article - (2023) Volume 11, Issue 3
Real Time Face Recognition using Haar Cascade Classifiers for Door Unlocking System
Abhishek Gupta* and Deepti MittalReceived: Apr 26, 2023, Manuscript No. ijcsma-23-97025; Editor assigned: Apr 28, 2023, Pre QC No. ijcsma-23-97025 (PQ); Reviewed: May 12, 2023, QC No. ijcsma-23-97025 (Q); Revised: May 19, 2023, Manuscript No. ijcsma-23-97025 (R); Published: May 26, 2023, DOI: 10.5281/zenodo.7993903
Abstract
In many automation systems it became difficult for human being to retrieve the large datasets and data analysis and the same in image analysis. Now-days face detection has great impact in our daily life communication systems. Hence, face detection system is one of the important technology and playing important role in face recognition. Face Detection and Recognition both have active research areas over the past few decades and have been proven effective in many applications such as computer security and artificial intelligence. Conventional method of identification based on the exclusive knowledge like a social security number or a password are not all together reliable. Somehow password can be forgotten or compromised. But a face is undeniably connected to its owner. It cannot be borrowed or stolen. The system can compare scans to records stored in a central or local database. The software first captures an image of all the authorized persons and stores the information into the database. Having many applications this project is mainly for future features like security, safety, monitoring and control to home automation. A day to day home security level grown up to provide security to our house based on face recognition can be implemented. A standard web camera to capture the image to identify the visitor. It’s a method that identifies the visitor. If the face recognizes visitor, the door will be unlocked or opened. If they are not identified door will not be unlocked. The system will perform detection and recognition rapidly in real time when face in front of camera. This project basic utilizes the camera, and raspberry pi system to create a door unlocking mechanism. If the user at the door is recognized, door will be unlocked.
passeio de bósforo em istambul
Keywords
ATM; CCTV; Haar Cascades; Pi 3 Deep Learning; Local Binary Patterns.
Introduction
Face detection is one of the important applications found in computer vision and it plays very important role in image processing due to its multidimensional applications such as facial expression detection, human computer interface and etc.
This work presents a design and framework for an unlocking of a door or an any security device mechanism using face recognition which tackles the problem of security. Fingerprint can be forged and password can be forgotten or hacked but a face is undeniably connected to the owner of face [1].
This system uses Haar Cascade technique along with Ada boot Algorithm for face detection, with Raspberry Pi as its core processing unit while using a 5 Mega Pixel camera to capture the face of the user. The system compares the face of the user with a pre-defined database of authorized owners and opens the door if the face matches with the image in the database. The face is scanned and compared in three different angles for maximum security and is equipped with a motion sensor which acts as a foolproof against images, pictures etc.
Disadvantages of Other Technologies for Security Systems
• RFID system
• Biometric finger print system
• Password or Pin
Haar Casacde
Haar Cascading is the machine learning method where a classifier is drilled from a great deal of positive and negative photos. The algorithm is put forwarded by Paul Viola and Michael Jones. Haar feature based cascade classifiers are the classifiers implemented for object detection. Face detection and facial expressions in an image are also successfully detected. The exercise is finished by offering positiveand negative pictures to the classifier [2].
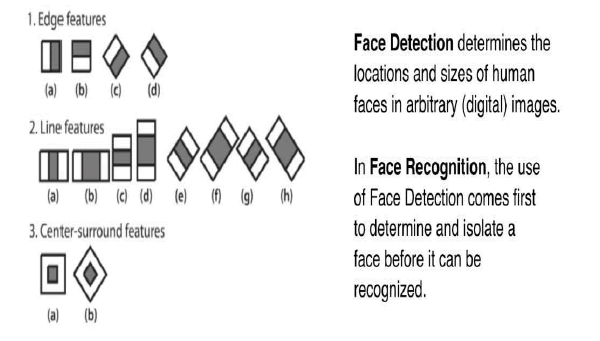
Haar Cascades use the Ada - boost learninglearning algorithm which selects a small number of important features from a large set to give an efficient result of classifiers then use cascading techniques to detect face in an image. Here are some Haar- Features (Figure 1).
Figure 1: Haar Feature Extraction Kernels.
Local Binary Patterns
Local Binary Pattern is a kind of visual course used for categorization on computer vision. LBP is the distinct case of the Texture Spectrum imitation put forwarded in 1990.
LBP was first illustrated in 1994. It has since been found to be a strong factor for texture categorization. By utilizing LBP operator, individual photo is examined as a structure of micro-patterns. Then the histogram of LBP is enumerated throughout the face, which encrypts just the circumstances of micro-patterns.
Literature Review
A model has developed which catches the live images from Camera. Then it applies different algorithms for face detection and face recognition. They also created the GUI on single click which catches the images, form the dataset and inculcate the dataset. They used the Haar cascade algorithm to recognize the face in the image [3].
Palanivel N et al. in 2019, has approach a module that signs the existence of people by detecting their facial nature and creating the attendance data itself. Face Recognition's reliability charge is bestrewed with the aspects similar to changing the glowing, posture changes, expression changes, and occlusion. They used K-means clustering algorithmic rule for analyzing the face characteristics. Biometric nature of the face features has been withdrawn. The K-mean clustering approach is used in gathering the face characteristics. Then, SVM method is used in detection of the photos characteristics. It may fulfill high identification showing with lesser characteristics number [4].
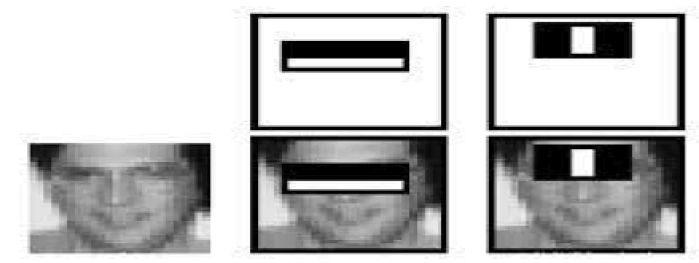
Omar Abdul Rhman Salim et al. in 2018, had proposed a technique of implementing a fully implanted student attendance process by face detection. The technique is depending on Raspberry Pi which runs Raspbian Operating System. The Camera and a 5-inch screen is connected to the Raspberry Pi. The image captured from the camera will be transferred to the Raspberry Pi. Which is intern programmed to handle face recognition by developing the LBPs. If the face in the input image i.e., image taken matches with the trained dataset image, the door will be opened and the attendance will be taken positively and it will be stored (Figure 2) [5].
Figure 2: Haar Like Feature
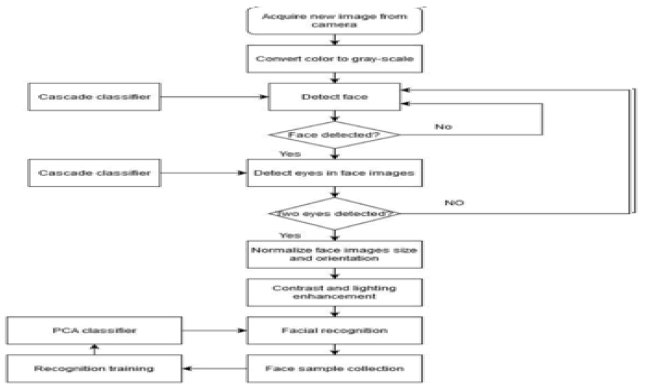
Figure 3 represents the flowchart of the Haar cascade classifier. Once the camera acquires the image it converts the image into gray-scale. The cascade classifier detects the face, if the face is detected then the classifier once again checks for the both eyes in the detected face and if two eyes are detected it normalizes the face images size and orientation. Then the image is processed for face recognition where the image is compared with the face sample collection.
Figure 3: The Flowchart of the Haar Cascade Classifier.
Methodology
The most important of feature of any home security system is to detect the people who enter or leave the house. Instead of monitoring that through passwords or pins unique faces can be made use of as they are one’s biometric trait. These are innate and cannot be modified or stolen easily. The level of security can be raised by using face detection
The proposed face recognition door lock security system has been developed to prevent robbery in highly secure areas like home environment with lesser power consumption and more reliable standalone security device for both Intruder detection and for door security.
This system is powered by raspberry pi circuit. Raspberry Pi electronic board is operated on Battery power supply, wireless internet connectivity by using USB modem, it includes camera, PIR motion sensor and a door. Whenever the person comes in front of the door, it recognizes the face and if it is registered then it unlocks the door, if the face is not registered it will raise an alarm and clicks a picture and send it on the registered number. This is how the system works [6].
Image Capture
A camera is placed away from the entrance to capture an image of the front of the student. And a further process goes for face detection.
Face Detection and Facial Features
The appropriate and effective facial detection algorithm constantly improves facial recognition. Several facial algorithms such as face-to-face geometry, construction methods, Face geometry- based methods, Feature Invariant methods, machine learning based methods. Out of all these methods Viola and Jones proposed a framework that gives a high detection rate and is also fast. Viola-Jones detection algorithm is fast and robust. So we chose ViolaJones face detection algorithm, which uses Integral Image and Ada Boost learning algorithm as classier. We have observed that this algorithm yields better results in a variety of lighting conditions.
Pre-Processing
Extracting the face features it is called pre- processing. This pre-processes step involves specifying the extracted facial image and transforms to 100 × 100. Histogram Equalization is the most commonly used Histogram Normalization technique. This improves the contrast of the image as it extends beyond the intensity of the image, making it even more clear and constraint.
Database Development
As we choose biometric based system every individual is required. This database development phase consists of an image capture of each individual and extracting the biometric feature, and then it is enhanced using preprocessing techniques and stored in the database.
Post-Processing
In the proposed system, after recognizing the faces of the person, the names are show into a video output. The result is generated by exporting mechanism present in the database system. These generated records can be seen in real time video. This ensures that person whose faces are not recognized correctly by the system have to check in database. Thus, giving them the ability to correct the system and make it more stable and accurate.
• Capture the Person’s Image.
• Apply Face detection algorithms to detect face.
• Use viola Jones and KLT algorithm extract the region of interest in rectangular bounding box.
• Convert to gray scale, apply histogram equalization and Resize to 100 × 100 i.e. apply pre- processing.
• If enrollment phase, then store in database else apply PCA (For Feature Extraction) end if Post-processing.
Face Detection using Cascade Classifiers in Open CV
Only if we are able to detect a face we will able to recognize it or remember it. To detect an object such as face Open CV uses something called Classifiers. These Classifiers are pre-trained set of data (XML File) which can be used to detect a particular object in our case a face. Apart from detecting face, classifiers can detect other objects like nose, eyes, vehicle license plate, smile etc.
Recognition
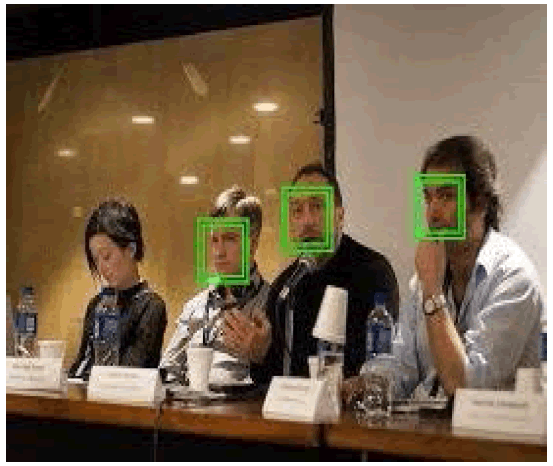
In recognition process the data of the user which is present in the data base is compared with the person data who is in front of the camera both data is compared by local binary patter histograms of two data if it matches then the person is recognized and go to further process. Else it displays unknown I'd (Figure 4).
Figure 4: Image Captured at Real Time
Conclusion
In this proposed door access security system by using face recognition the images are stored in a data base. This system uses door lock access for residential and commercial Purposes. Here we have designed a highly secured door locking system by using Raspberry pi.
Concern persons will be informed successfully about the person detection along with details attached.
Face recognition is one of the several techniques for recognizing people. There are several methods that can be used for that purpose. Some of the most common are using PCA or Eigen faces. Though there are other new techniques more simple to understand the use and implement but also with very good performance. The Haar Cascades algorithm is one of those algorithms. As we show Haar Cascades has very good performance and is very accurate.
The complete door unlocking system is implemented in Open CV. This door access system shows the use of facial recognition techniques for the purpose of security
Future Scope
• Deliver a practical and workable solution that addresses the requirements of the regulatory authorities.
• Limit the financial risks given that they were forced to take responsibility for financial loss.
• Take societal responsibility to reduce rising levels of crime.
• Increase customer satisfaction.
• Peace of mind given the higher level of security applied.
References
- Yang, D., et al. "An emotion recognition model based on facial recognition in virtual learning environment." Procedia Comput. Sci. 125; 2-10, (2018).
- Kazanskiy, N., et al. "Performance analysis of real-time face detection system based on stream data mining frameworks." Procedia Eng. 201, 806-816, (2017).
- Ibrahim, R., and Zalhan M. Z. "Study of automated face recognition system for office door access control application." 2011 IEEE 3rd Int Conf Commun Softw Netw., IEEE, 2011.
- Fan, X., et al. "The system of face detection based on OpenCV." 2012 24th Chin Control Decis Conf (CCDC). IEEE, 2012.
- Lienhart, R., and Jochen M. "An extended set of haar-like features for rapid object detection." Proceedings. int conf image process. Vol. 1. IEEE, 2002.
- Archana, T., T. et al. "Multiple face detection in color images." 2015 Int. Conf Signal Process Commun Eng Syst, IEEE, 2015.